This article was updated to reflect the Cybersecurity Maturity Model Certification (CMMC) Programmatic final rule, which went into effect December 16, 2024.
As a Registered Practitioner Organization (RPO) and a CMMC Third-Party Assessment Organization (C3PAO), Cherry Bekaert helps clients prepare for CMMC certification assessments and assesses clients via the CMMC certification assessment process. Below, we provide answers to frequently asked questions (FAQs) surrounding CMMC preparation and compliance.
What Is CMMC?
The Cybersecurity Maturity Model Certification (CMMC) is a unified cybersecurity standard for Department of Defense (DoD) acquisitions aimed at securing the Defense Industrial Base (DIB) supply chain. It is a DoD program established to verify contractors have implemented the required security measures necessary to safeguard federal contract information (FCI) and controlled unclassified information (CUI).
The CMMC Program is designed to provide increased assurance to the DoD that defense contractors and subcontractors are compliant with information protection requirements for FCI and CUI, and are protecting such information at a level commensurate with risk from cybersecurity threats, including Advanced Persistent Threats (APTs). The CMMC Program rule will allow the DoD to confirm a defense contractor or subcontractor has implemented the security requirements for a specified CMMC level and is maintaining that status (meaning level and assessment type) across the contract period of performance. The goal of which is to secure the Defense Industrial Base (DIB) supply chain against evolving cybersecurity threats.
Why Is CMMC Important?
The CMMC Program is designed to enforce the protection of FCI and sensitive CUI, shared within the DIB. The framework is intended to:
- Safeguard sensitive information to enable and protect the warfighter
- Enforce DIB cybersecurity standards to meet evolving cybersecurity threats
- Ensure accountability while minimizing barriers to compliance with DoD requirements
- Perpetuate a culture of cybersecurity and cyber resilience throughout the DIB supply chain
- Flow-down requirements for subcontractors handling FCI and/or CUI
While contractors may bid on DoD contracts with CMMC requirements, compliance with CMMC is required to receive contract awards.
What Are the CMMC Requirements and CMMC Levels?
CMMC requirements include:
- FAR 52.204-21, Basic Safeguarding of Covered Contractor Information Systems
- NIST SP 800-171 Rev 2, Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations
- A subset of the requirements from NIST SP 800-172, Enhanced Security Requirements for Protecting Controlled Unclassified Information: A Supplement to NIST Special Publication 800—171
The CMMC Model consists of three levels and can require an independent assessment by an authorized third-party assessment organization (C3PAO). The three levels include:
- CMMC Level 1 — Basic safeguarding of FCI
- CMMC Level 2 — Protecting CUI
- CMMC Level 3 — Protecting CUI and reducing risk of advanced persistent threats (APT)
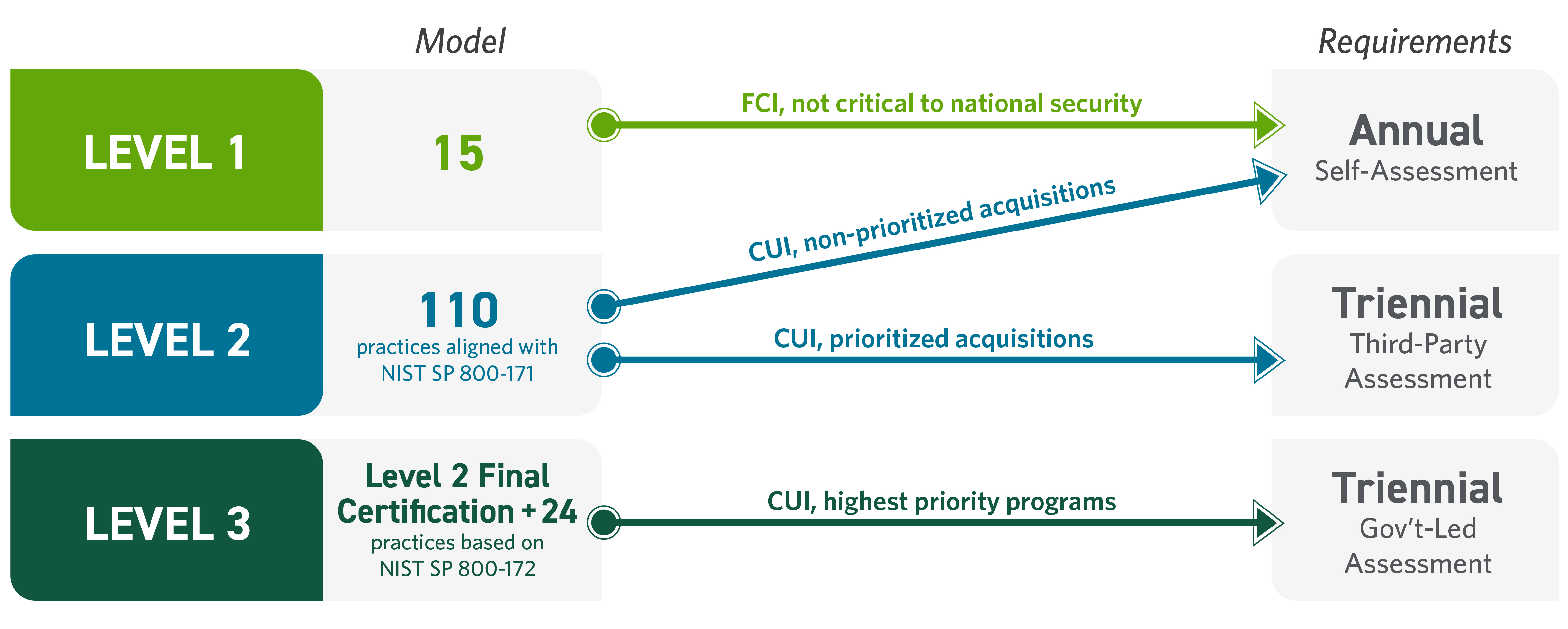
The security requirements in CMMC Level 1 are those set forth in FAR clause 52.204-21(b)(1)(i) – (b)(1)(xv). The security requirements in CMMC Level 2 are identical to the requirements in NIST SP 800-171 r2. Lastly, the security requirements in CMMC Level 3 include the requirements in NIST SP 800-171 r2, selected from NIST SP 800-172, Feb2021, and where applicable, Organization-Defined Parameters (ODPs) are assigned. Table 1 to § 170.14(c)(4) of the rule identifies the selected requirements and applicable ODPs.
The CMMC Program does not alter any separately applicable requirements to protect FCI or CUI, including those requirements in accordance with 48 CFR 52.204-21, or covered defense information in accordance with 48 CFR 252.204-7012, Safeguarding Covered Defense Information and Cyber Incident Reporting, or any other applicable information protection requirements. The CMMC Program provides a means of verifying implementation of the security requirements set forth in 48 CFR 52.204-7021, NIST SP 800-171 r2, and NIST SP 800-172, Feb2021, as applicable.
Who Does CMMC Apply To?
The CMMC Program requirements apply to all DoD contract and subcontract awardees that, in performance of the DoD contract, will process, store or transmit information that meets the standard for FCI and CUI on unclassified contractor information systems.
Further, the CMMC Program requirements may apply to private-sector businesses or other CMMC Assessment and Certification Ecosystem entities, including cloud service providers (CSPs) and external service providers (ESPs).
A CSP is an external company that provides services based on cloud computing as defined in NIST SP 800-145, Sept 2011. An ESP consists of external people, technology or facilities that an organization utilizes for the provision and management of IT and/or cybersecurity services on behalf of the organization. In the CMMC Program, CUI or security protection data must be processed, stored or transmitted on the ESP assets to be considered an ESP.
Additionally, the CMMC Program requirements will apply to new DoD solicitations and contracts and will flow down to subcontractors who process, store or transmit FCI and CUI in performance of the subcontract. See the table below for flow-down requirements.
|
Prime Contractor Requirement |
Minimum Requirement if the Subcontractor Will Process Store, or Transmit |
|
|
FCI |
CUI |
|
|
Level 1 (Self) |
Level 1 (Self) |
N/A |
|
Level 2 (Self) |
Level 1 (Self) |
Level 2 (Self) |
|
Level 2 (C3PAO) |
Level 1 (Self) |
Level 2 (C3PAO) |
|
Level 3 (DIBCAC) |
Level 1 (Self) |
Level 2 (C3PAO) |
The requirements of the rule do not apply to federal information systems operated by contractors or subcontractors on behalf of the government. Additionally, in very limited circumstances and in accordance with all applicable policies, procedures, and requirements, a service acquisition executive or component acquisition executive in the DoD, or as delegated, may elect to waive the inclusion of CMMC Program requirements in a solicitation or contract. In such cases, contractors and subcontractors must comply with all applicable cybersecurity and information security requirements.
When Will CMMC Be Enforced?
Now that the CMMC Program, CFR 32 Part 170, rule has been published to the Federal Register and went into effect on December 16, 2024, C3PAOs granted reauthorization can commence CMMC Level 2 certification assessments and issue Level 2 certificates of CMMC Status independent of the Defense Contractor Management Agency’s (DCMA) Defense Industrial Base Cybersecurity Assessment Center (DIBCAC).
CMMC will not be enforced in contracts until the acquisition rule, 48 CFR 252.204-7021, Cybersecurity Maturity Model Certification Requirements, is finalized and published to the Federal Register. Once 48 CFR 252.204-7021 goes into effect, there will be a phased implementation approach to enforce the CMMC requirements. 48 CFR 252.204-7021 is not expected to go into effect until mid-2025.
Once 48 CFR 252.204-7021 becomes effective, certain DoD contractors handling FCI and CUI will be required to achieve a CMMC Status at the applicable level as a condition of contract award. CMMC requirements will be implemented using a four-phase implementation plan over a three-year period. The table below outlines DoD’s four implementation phases.
|
Phase |
Summary |
Timeline |
|
Phase 1 |
|
Begins on the effective date of 48 CFR 252.204-7021, the CMMC Acquisition final rule. |
|
Phase 2 |
|
Begins one calendar year following the start date of Phase 1. |
|
Phase 3 |
|
Begins one calendar year following the start of Phase 2. |
|
Phase 4 |
|
Begins one calendar year following the start date of Phase 3. |
How Do I Know What Level My Organization Needs to Achieve?
DoD program managers or requiring activities are responsible for selecting the CMMC Status that will apply for a particular procurement or contract. Selection of the applicable CMMC Status will be based on factors including but not limited to:
- Criticality of the associated mission capability
- Type of acquisition program or technology
- Threat of loss of the FCI and CUI to be shared or generated in relation to the effort
- Impacts from the exploitation of information security deficiencies
- Other relevant policies and factors, including Milestone Decision Authority (MDA) guidance
The required CMMC level and assessment type will be specified in the solicitation and resulting contract. Questions about the CMMC level required by the solicitation should be directed to the contracting officer. Once CMMC is implemented through 48 CFR, 252.204-7021 the rollout of the CMMC Program can occur. Contractors handling FCI or CUI will be required to meet the CMMC requirement specified in the contract.
DoD contractors and subcontractors that handle FCI will be required to demonstrate CMMC Status of Final Level 1 (Self).
DoD contractors and subcontractors that handle CUI will be required to meet CMMC Status of Final Level 2 (Self) or CMMC Status of Final Level 2 (C3PAO).
DoD contractors and subcontractors managing CUI within DoD’s highest priority programs will be required to meet CMMC Status Level 3 (DIBCAC).
Additionally, the CMMC Program requirements will apply to new DoD solicitations and contracts and will flow down to subcontractors who process, store or transmit FCI and CUI in the performance of the subcontract. The table below defines the CMMC flow-down requirements for subcontractors.
|
Prime Contractor Requirement |
Minimum Requirement if the Subcontractor Will Process Store or Transmit |
|
|
FCI |
CUI |
|
|
Level 1 (Self) |
Level 1 (Self) |
N/A |
|
Level 2 (Self) |
Level 1 (Self) |
Level 2 (Self) |
|
Level 2 (C3PAO) |
Level 1 (Self) |
Level 2 (C3PAO) |
|
Level 3 (DIBCAC) |
Level 1 (Self) |
Level 2 (C3PAO) |
What Are the Requirements for Cloud Service Providers?
Under certain circumstances, an OSA may use a cloud environment to process, store or transmit CUI in performance of a contract or subcontract. DFARS 252.204-7012 states that if a contractor intends to use an external cloud service provider to store, process or transmit any covered defense information (CUI) in performance of a contract, the contractor shall require and ensure that the cloud service provider meets security requirements equivalent to those established by the Government for the Federal Risk and Authorization Management Program (FedRAMP) Moderate baseline.
Additionally, the contractor must ensure that the cloud service provider complies with requirements in paragraphs (c) through (g) of the clause for cyber incident reporting, malicious software, media preservation and protection, access to additional information and equipment necessary for forensic analysis and cyber incident damage assessment. The CMMC Program rule allows contractors and subcontractors to use CSPs under the following circumstances:
- The CSP product or service offering is FedRAMP Authorized at the FedRAMP Moderate (or higher) baseline, in accordance with the FedRAMP Marketplace
- The CSP product or service offering is not FedRAMP Authorized at the FedRAMP Moderate (or higher) baseline but meets security requirements equivalent to those established by the FedRAMP Moderate (or higher), in accordance with DoD Policy
- The OSA’s on-premises infrastructure connecting to the CSP’s product or service offering is part of the CMMC Assessment Scope
What Are the Requirements for External Service Providers?
The use of the ESP, its relationship to the Organization Seeking Certification (OSA), and the services provided must be documented in the OSA’s System Security Plan (SSP) and described in the ESP’s service description and customer responsibility matrix (CRM). The ESP services used to meet OSA requirements are assessed within the scope of the OSA’s assessment against all applicable Level 2 and/or 3 security requirements. ESPs are able to obtain their own CMMC Level 2 or 3 certification assessment, which can be inherited by the OSA for the applicable requirements noted in the OSA’s CRM.
How Do I Comply with the Applicable CMMC Level?
CMMC Level 1 Self-Assessment
To comply with CMMC Level 1 self-assessment requirements, the OSA must complete and achieve a MET result for all of the applicable security requirements set forth in 48 CFR 52.204-21(b)(1)(i) through (xv) to achieve the CMMC Status of Final Level 1 (Self). No POA&Ms are permitted for CMMC Level 1. The OSA must conduct a self-assessment and submit assessment results to the Supplier Performance Risk System (SPRS).
To maintain compliance with the requirements for the CMMC Status of Final Level 1 (Self), the OSA must conduct a Level 1 self-assessment on an annual basis and submit the results in SPRS, or its successor capability.
The self-assessment must be scored in accordance with the CMMC Scoring Methodology, must be performed in accordance with the CMMC Level 1 scope requirements and must be performed using the objectives defined in NIST SP 800-171A Jun2018 for the security requirement that maps to the CMMC Level 1 security requirement.
CMMC Level 2 Self-Assessment
To comply with CMMC Level 2 self-assessment requirements, the OSA must complete and achieve a MET result for all security requirements specified in NIST SP 800-171 r2 to achieve the CMMC Status of Level 2 (Self). The OSA must conduct a self-assessment and submit assessment results in SPRS.
To maintain compliance with the requirements for a CMMC Status of Level 2 (Self), the OSA must conduct a Level 2 Self-Assessment every three years and submit the results in SPRS, within three years of the CMMC Status Date associated with the Conditional Level 2 (Self). Additionally, an affirming official at the OSA must submit an annual CMMC affirmation attesting to continuing compliance with all requirements of the CMMC Status Level 2 (Self).
The self-assessment must be scored in accordance with the CMMC Scoring Methodology, must be performed in accordance with the CMMC Level 2 scope requirements and must be performed using the objectives defined in NIST SP 800-171A, Jun2018. Artifacts used as evidence for the assessment must be retained by the OSA for six years from the CMMC Status Date.
Plan of Actions and Milestones (POA&M) are allowed in a Level 2 self-assessment. A POA&M closeout assessment must be performed by the OSA when all NOT MET requirements have been remediated. The POA&M closeout self-assessment must be performed within 180 days of the Conditional CMMC Status Date.
CMMC Level 2 Certification Assessment
To comply with CMMC Level 2 certification assessment requirements, the OSC must complete and achieve a MET results for all the requirements specified in NIST SP 800-181 r2 to achieve the CMMC Status of Level 2 (C3PAO). The OSC must obtain a Level 2 certification assessment from an authorized or accredited C3PAO following the procedures outlined in NIST SP 800-171A, Jun2018. The C3PAO must submit the Level 2 certification assessment results into the CMMC instantiation of eMASS, which then provides automated transmission to SPRS.
To maintain compliance with the requirements for a CMMC Status of Level 2 (C3PAO), the Level 2 certification assessment must be complete within three years of the CMMC Status Date associated with the Conditional Level 2 (C3PAO). Additionally, an affirming official at the OSC must submit an annual CMMC affirmation attesting to continuing compliance with all requirements of the CMMC Status Level 2 (C3PAO).
POA&Ms are allowed during a Level 2 certification assessment in accordance with the CMMC POA&M requirements. The OSC must remediate any requirements that are not met and must undergo a POA&M closeout certification assessment from a C3PAO. The C3PAO must post compliance results into the CMMC instantiation of eMASS within 180 days of the CMMC Status Date associated with the Conditional Level 2 (C3PAO).
If the POA&M is not successfully closed out within the 180-day timeframe, the information system's Conditional Level 2 (C3PAO) CMMC Status will expire. The OSC has achieved the CMMC Status of Final Level 2 (C3PAO) if the Level 2 certification assessment results in a passing score based on the CMMC Scoring Methodology.
CMMC Level 3 Certification Assessment
To comply with CMMC Level 3 certification assessment requirements, the OSC must achieve a CMMC Status of Final Level 2 (C3PAO) on the Level 3 CMMC Assessment Scope, prior to initiating a Level 3 certification assessment, which will be performed by DCMA DIBCAC on behalf of the DoD. The OSC initiates a Level 3 certification assessment by emailing a request to DCMA DIBCAC point of contact. The OSC must complete and achieve a MET result for all selected security requirements from NIST SP 800-172, Feb2021 to achieve the CMMC Status of Level 3 (DIBCAC).
To maintain compliance with the requirements for a CMMC Status of Level 3 (DIBCAC), the Level 3 certification must be performed every three years for all information systems within the Level 3 CMMC Assessment Scope. In addition, given that compliance with Level 2 requirements is a prerequisite for applying CMMC Level 3, a Level 3 (C3PAO) certification must also be conducted every three years to maintain CMMC Level 3 (DIBCAC) status. Level 3 certification must be completed within three years of the CMMC Status Date associated with the Final Level 3 (DIBCAC), or if there was a POA&M, within three years of the CMMC Status Date associated with the Conditional Level 3 (DIBCAC). Additionally, an affirming official at the OSC must submit an annual CMMC affirmation attesting to continuing compliance with all requirements of the CMMC Status 2 (C3PAO) and Level 3 (DIBCAC).
POA&Ms are allowed during a Level 3 certification assessment in accordance with the CMMC POA&M requirements. The OSC must remediate any requirements that are not met and must undergo a POA&M closeout certification assessment from DCMA DIBCAC. The DCMA DIBCAC must post compliance results into the CMMC instantiation of eMASS within 180 days of the CMM Status Date associated with the Conditional Level 3 (DIBCAC). The OSC has achieved the CMMC Status of Final Level 3 (DIBCAC) if the Level 3 certification assessment results in a passing score based on the CMMC Scoring Methodology.
How Do I Prepare for CMMC Certification?
Preparation is the key to success. Companies should begin preparing for a CMMC assessment now by assessing their readiness to achieve the appropriate CMMC level. Given the rigorous requirements, CMMC may take longer than many companies realize, so readiness and preparation are key to success. Cherry Bekaert is an RPO and an authorized C3PAO by the Cybersecurity Maturity Model Certification Accreditation Body, Inc. (The Cyber AB). As an RPO, we assist OSAs with CMMC readiness assessments for Levels 1, 2 and 3.
- The main areas companies should focus on to prepare for a CMMC assessment include:
- Identifying the correct CMMC Level of certification required
- Identifying where FCI and CUI data is stored, processed and transmitted within the contractor’s systems
- Identifying and documenting the assessment scope based on the CMMC Level 1, 2 or 3 Scoping Guidance, defining:
- System boundaries
- CUI data flow
- Asset inventory external system connections, including ESPs and CSPs
- Asset categorization
- Data flow, including any out-of-scope assets
- Completing a gap analysis against the applicable security requirements at the appropriate CMMC level to assess the current state of compliance and identify gaps that will need to be remediate prior to the assessment.
- Developing a roadmap to address gaps identified from the gap analysis
- Developing CMMC program documentation to support the contractor’s compliance program, including:
- System security plan
- Shared responsibility matrix
- Incident response plan
- Supporting policies, procedures and standards
- Conduct a self-assessment. Contractors are required to complete a self-assessment before undergoing the certification assessment conducted by an authorized C3PAO.
Businesses should approach CMMC preparation with effort and vigor, as many companies underestimate the time and resources the process requires. CMMC readiness is not a process where most organizations can bid on a contract and quickly prepare and obtain the necessary certification to be awarded the contract within 30 to 60 days.
Based on experience, the majority of companies should allow at least six months of preparation time. However, that timeframe will vary depending on the current state and complexity of the assessed environment.
What are the Differences Between DFARS 252.204-7012 and DFARS 252.204-7021?
To date, defense contracts involving the development or transfer of CUI to a non-government organization require applicable requirements of DFARS clause 252.204-7012. This clause requires defense contractors to provide adequate security on all covered contractor information systems by implementing the 110 security requirements specified in NIST SP 800-171 r2.
This clause includes additional requirements; for example, defense contractors must confirm that any CSPs used by the contractor to handle CUI meet FedRAMP Moderate Baseline or the equivalent requirements. It also requires contractors to implement certain cyber incident reporting requirements per paragraph (c) through (g). Further, the clause requires defense contractors to flow all the requirements down to their subcontractors who process, store or transmit CUI.
To comply with DFARS clause 252.204-7012, contractors are required to develop an SSP detailing the policies and procedures their organization has in place to comply with NIST SP 800-171 r2. The SSP serves as a foundational document for the required NIST SP 800-171 r2 self-assessment.
To comply with 48 CFR 252.204-7019 (DFARS provision 252.204-7019) and DFARS clause 252.204-7020, self-assessment scores must be submitted. The highest score is 110, meaning all 110 NIST SP 800-171 r2 security requirements have been fully implemented. If a contractor's Supplier Performance Risk System (SPRS) score is less than 110, indicating security gaps exist, then the contractor must create a plan of action identifying security tasks that still need to be accomplished.
In essence, an SSP describes the cybersecurity plan the contractor has in place to protect CUI. The SSP needs to address each NIST SP 800-171 r2 security requirement and explain how the requirement is implemented. This can be through policy, technology or a combination of both.
The CMMC Program is not a verification program for compliance with all requirements of DFARS clause 252.204-7012. Rather, its purpose is to ensure compliance with FAR clause 52.204-21, NIST SP 800-171 r2, and NIST 800-172 Feb2021, when applicable. The CMMC Program does not assess the cyber incident reporting requirements, paragraphs (c) through (g) of DFARS clause 252.204-7012.
It should be noted that the CMMC Program does have specific assessment requirements for CSPs and ESPs. The CMMC assessment framework will not alter, alleviate or replace the cyber incident reporting or other aspects of DFARS clause 252.204-7012, which will remain effective where applicable.
Are CMMC Level 2 Certification Assessments Available?
The final CMMC Program rule went into effect on December 16, 2024. Reauthorized C3PAOs can begin to conduct CMMC Level 2 certification assessments. The DCMA DIBCAC’s Joint Surveillance Program is no longer assessing Organizations Seeking Certification. There is expected to be a high level of demand, given the number of contractors and subcontractors supporting the DIB. As a reauthorized C3PAO, Cherry Bekaert is ready to conduct CMMC Level 2 certification assessments. Reach out to our Information Assurance and Cybersecurity team to schedule your certification assessment.
Contact Us
If you have any questions regarding CMMC, Cherry Bekaert’s Information Assurance & Cybersecurity and Government Contracting advisors are available to discuss your situation with you.
Related Insights
- Podcast: CMMC Program Proposed Rule Published in the Federal Register: Insights Into the Proposed Rule and When CMMC 2.0 Will Be Required
- Podcast: Final CMMC Rule Reaches Critical Milestone
- Podcast: How Will NIST Special Publication (SP) 800-171, Revision 3 Impact CMMC?
- Article: Updated Projected Timeline for CMMC: What this Means for Contractors and How to Prepare for Certification
- Podcast: Final CMMC Rule: March 2023 Update
- Podcast: CMMC 2.0 – Where Does It Stand?
- Podcast: What’s New with CMMC 2.0?: August 2022 Update
- Podcast: CMMC 2.0 Brings Major Program Changes
- On-Demand Webinar: CMMC 2.0 Brings Major Program Changes
References
- 48 CFR 52.204-21, Basic Safeguarding of Covered Contractor Information Systems
- DFARS Clause 252.204-7012: Safeguarding Covered Defense Information and Cyber Incident Reporting
- DFARS Clause 252.204-7019: Notice of NIST SP 800-171 DoD Assessment Requirements
- DFARS Clause 252.204-7020: NIST SP 800-171 DoD Assessment Requirements
- DFARS Clause 252.204-7021: Cybersecurity Maturity Model Certification Requirements
- CFR 32 Part 170 CMMC Program Rule
- DoD CIO Memo: FedRAMP Moderate Equivalency for Cloud Service Provider’s Cloud Service Offerings
- CMMC Level 1 Scoping Guidance
- CMMC Level 1 Self-Assessment Guide
- CMMC Level 2 Scoping Guidance
- CMMC Level 2 Assessment Guide
- CMMC Level 3 Scoping Guidance
- CMMC Level 3 Assessment Guide
- NIST SP 800-171 Rev. 2: Protecting CUI in Nonfederal Systems
- NIST SP 800-171A: Assessing Security Requirements for Controlled Unclassified Information
- NIST SP 800-172: Enhanced Security Requirements for Protecting Controlled Unclassified Information
- NIST SP 800-172A: Assessing Enhanced Security Requirements for Controlled Unclassified Information
- NIST 800-145: The NIST Definition of Cloud Computing
- CMMC Accreditation Body Website: CMMC Accreditation Body
- FedRAMP Marketplace






